Canadian businesses are constantly at risk from cyber threats, and the impact of a cyber breach is devastating to business operations.
In 2017, Statistics Canada found that:
- 54% of businesses who suffered from an attack saw their day-to-day operations suffer
- 30% of businesses experienced financial loss after a breach
- 10% of impacted businesses lost revenue
Having a system for identifying and addressing cyber threats is a crucial part of risk management for businesses. And with businesses facing cyber threats more than ever before, the need for remediation processes and a cyber security remediation plan is critical.
What is Cyber Security Remediation?
Cyber security remediation is a structured approach to identifying and mitigating IT security threats. It’s a plan designed to help you detect issues before they take hold of your system and resolve issues that have already done damage.
Companies without adequate cyber security defenses are considered “soft targets” for threat actors, which means that they’re easy prey for criminals who want to make a quick buck and move on. Phishing scams, ransomware, and malware that avoid antivirus software are all examples of common attack avenues.
A recent study by Trustwave, 2020 Global Security Report, highlighted some of the top industries and environments impacted by cyber threats.
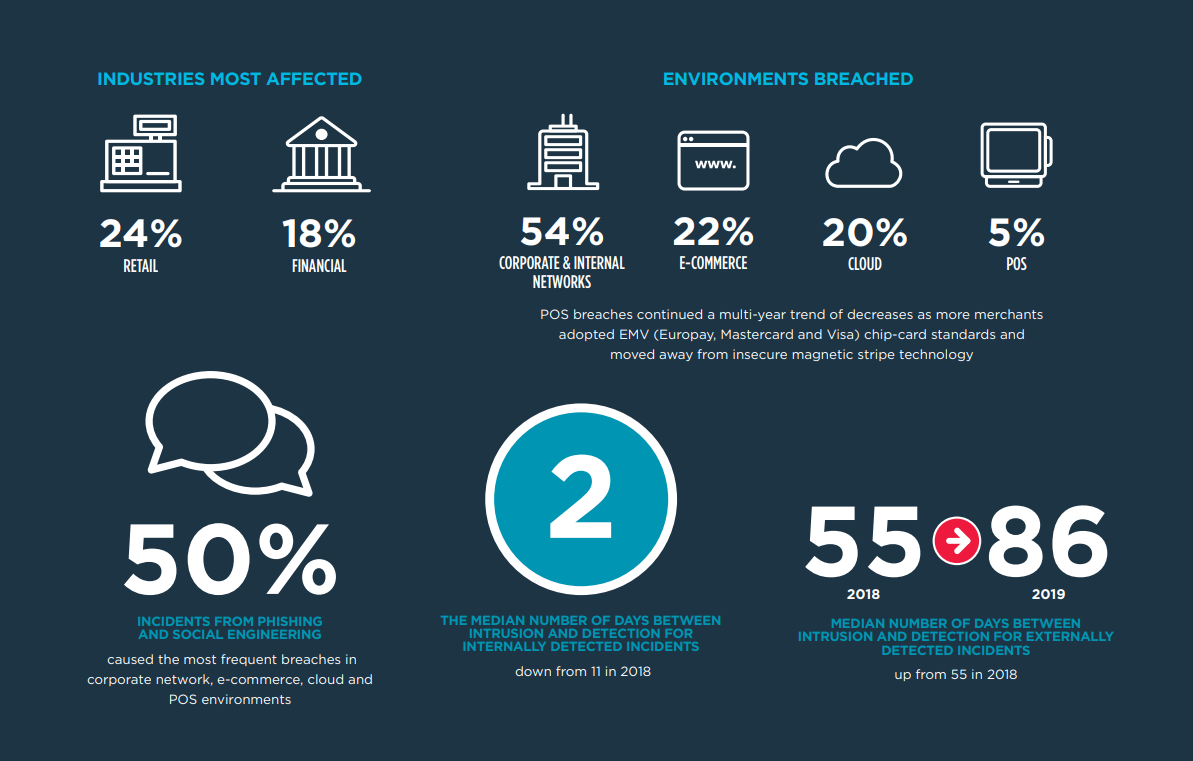
Image source: https://trustwave.azureedge.net/media/16717/2020-trustwave-global-security-report.pdf?rnd=132319806410000000
With companies on the line, business owners need to get proactive about vulnerability management and address the biggest threats facing their operations. To help you along, here are five basic steps you can take to help identify and resolve threats.
Cyber Security Threat Remediation
1. Perform a Baseline Security and Risk Assessment
The process begins with an audit of your current IT environment. You need to know where you’re most vulnerable to set up a proper defense. This begins with a full review of your system assets, processes, and operations as part of your baseline risk assessment.
Broadly, you’ll want to cover the following areas, at a minimum:
- Infrastructure scan of devices connected to your network
- Existing security architecture, programs, firewall configuration, or threat detection systems
- Review of your antivirus standards, patching process, and wireless networks configuration
- If applicable, the IT security vendors who provide services and their processes, policies, and strategies for threat remediation
- Internal policies for managing identified threats, disaster recovery options, and which employees are responsible for your vulnerability management system
2. Establish a Monitoring Process
The next step is to set up a system of continuous monitoring that alerts you to potential issues.
This is particularly important for businesses with broad numbers of unsecured laptops, smartphones, or other internet-enabled devices. The more unmonitored endpoints you have, the more likely you’ll experience data breaches – particularly when security isn’t an organizational priority.
From your above audit, make a list of all security vendors, programs, and platforms you have running in your IT security ecosystem. From there, keep a running tab of any updates from these vendors regarding new threats or security patches that may need to be addressed.
This is all part of your active monitoring process, which is designed to proactively warn you of threats before they become serious problems, and gives you good incident response times when a cyber attack occurs.
3. Apply Solutions to Identified Vulnerabilities
Use the collected information from your risk assessment audit and your monitoring workflows to take an active approach to the threat remediation process.
This step includes charting known vulnerabilities, assigning levels of risk to each issue, estimating the effort required to resolve, and coming up with a plan for addressing the issue that aligns with your IT system configurations.
Work with your vendors, IT staff, and established security teams to make sure all the bases are covered with the right security solutions.
Interested in learning more? Check out these blogs:
- Critical cybersecurity strategies for SMEs
- Practical cyber security for your business
- Cyber threats and how to defend your business against them
4. Train Employees in Security Remediation Best Practices
That same study by Trustwave found that, “50% of all cyber threats began from phishing and social engineering”. That means that employees were responsible for falling prey to cyber-criminal attempts to leverage their way past other security measures.
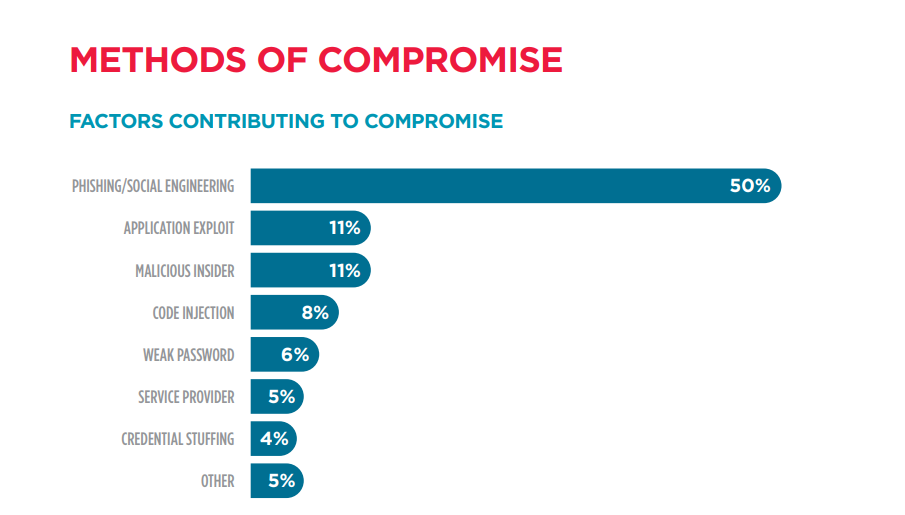
Make sure your employees are given security awareness training as a part of your cyber security plans. A company’s employees are often one of the weakest points in the security chain – something that threat actors understand well.
5. Rinse and Repeat as Needed
In the final step, repeat the above process regularly to guarantee ongoing security and to achieve the best vulnerability remediation.
Your cyber security remediation plan isn’t a one-off deal; it’s an ongoing process that needs to be reviewed numerous times to stay on top of your IT environment throughout your business’s operation. Come up with a plan based on the above steps, and stick to it until you’re confident in your security infrastructure.
*6. Plan for Security Remediation and Response
As an additional step, while remediating security risks is the top priority, it is also essential to plan for the possibility that a security risk gets past your defences. Learning How to Create an Incident Response plan, that details which roles, scenarios, steps, communication, and reporting is required in case of a cyber security event is a crucial preparation activity that will allow your organization to respond effectively should one occur.
Stay Ahead of Potential Threats with Security Services
If you need help getting started, use a security remediation plan template to kick things off.
If you want to develop a more personalized vulnerability assessment, it pays to work with a qualified cyber security vendor, like Resolute Technology Solutions, that can apply their industry expertise to your system. Or investigate if Managed Security Services are the right fit for your business for ongoing monitoring, response, and remediation. There are a variety of Managed Security Services that provide 24x7x365 coverage such as Managed Detection and Response (MDR) services. MDR services ensure systems, processes and security experts can detect and respond to cyber threats within minutes before they can breach your defenses.








