Cyberattacks can happen anytime, especially in the digital age when everyone can access anything online. This is significantly important for small to medium businesses, as it was found in 2023 that 61% of SMBs were hit by cybercrime. Investing in a stronger cybersecurity strategy and security measures can pay off, considering how fast technology and AI continue to evolve for criminal activities.
What is a Cybersecurity Strategy?
A cybersecurity strategy is an organization’s plan of action to safeguard information and computer systems against any cyber threat that may occur at any time. This strategy includes the duties of individuals and teams to protect a business from malware, phishing attacks, data breaches, and other cyber attacks.
There are many types of data cyber attacks can steal. This includes:
- Credit card information
- Your business and client’s banking details
- Product designs and files
- Intellectual property
Getting any of this leaked, especially for small to medium businesses can be devastating. Financial loss, legal battles, compromised business, and, ultimately, reputational damage are just some of the ways cyber threats can impact customers and your business.
A study from 2022 found that 30% of small businesses fell victim to cybersecurity attacks before COVID, while 28% were attacked when the pandemic hit. Though less than half weren’t affected by malicious attacks, the risk remains of cyber attacks happening to your business. Fortunately, implementing regular updates and upgrades to your cybersecurity strategy can help keep it effective in protecting your business.
Key Components of a Cybersecurity Strategy
Having the right guidelines and safety measures to prevent, detect, and recover from cyber incidents is a crucial step to reducing risk to your business. Every business should consider implementing these key components for a truly effective cybersecurity strategy.
- Risk assessment
Risk mitigation efforts matter. Assess the chance of threats and how they might impact your business to inform how you can prioritize and allocate the right measures for threats. This includes identifying assets, threats, and any vulnerabilities that may be exploited. - Policy development
A policy can serve as a guiding light for standards and security measures. Developing and implementing policies can also better inform how employees and stakeholders utilize and protect IT resources and sensitive data. - Preventive controls
Ensuring you have security measures for preventive controls like firewalls, antivirus, and hardware and software configurations will go a long way toward preventing cyber incidents. These can cover unauthorized access, data breaches, and attacks. - Detection and response
Real-time detection is a proactive approach to effectively detecting cybersecurity incidents. With the right detection and incident response plan, you can work more efficiently to minimize the volume of impact and secure your business. - Recovery plans
After responding to cyber incidents, a strategy for restoring any damage can speed up the recovery of collateral damage. This means having processes for fixing impaired services or compromised customer accounts can help build and regain customer trust and loyalty.
Understanding Your Current Cybersecurity Strategy
Evaluating your current cybersecurity strategy is crucial to identifying strengths and weaknesses. This helps determine areas that require improvement or updating to ensure your processes are up-to-date and effective.
- Review current policies and procedures
Start off by taking a closer look at all your current cybersecurity policies, procedures, and guidelines. Assess whether your documents are clear, updated, and aligned with your business objectives and compliance requirements. - Identify protected assets
Taking inventory of all critical assets in your organization. Both tangible and intangible count, this includes everything from data to hardware, devices, software, services and even applications. These are all valuable to the function of your organization and each may require varying levels of protection. - Assess current security measures
Evaluating your security measures will help you decide what needs updating or upgrading. This includes firewalls, antiviruses for software, encryption, security controls, and intrusion detection systems. - Understand threat landscape
As technology advances, so does the capacity for cyber threats to grow more sophisticated. Analyze the external and internal risks in the cyber threat landscape relevant to your business and see where your vulnerabilities are. Staying informed with the latest cybersecurity threats will help you select what updates are truly necessary to protecting your assets. - Analyze security culture and awareness
Every organization needs employee awareness on cybersecurity. If you conduct regular training, see if your resources are up-to-date on best practices to maintain truly effective security measures.
How to Upgrade Your Cybersecurity Strategy
There are many ways you can build your cybersecurity strategy. What will make a real difference is ensuring you enforce a proactive approach for a more effective security strategy.
Here are some ways to upgrade your framework to anticipate and brace for the worst.
- Inform and educate your users
Your clients or users are also prone to cyber-attacks. Similar to employees, clients should also be familiar on what to watch out for when threats or attacks happen. Phishing attacks in 2023, for example, led to 16% of company data breaches as a direct result.
Cultivating user awareness by sending informative content on cyber threats and enrolling in security awareness training will help your clients steer clear of malicious attempts.
- Enforce malware prevention measures
Malware prevention can safeguard your business’s IT infrastructure and data. Aside from implementing the principle of least privilege, you can reduce the risk of unauthorized access with multi-factor authentication (MFA), robust endpoint protection, and regular software and operating systems updates through patch management.
- Invest in an AI-powered Authentication
Artificial intelligence is a useful tool that can benefit businesses in many ways. Working with AI-powered authenticators enables you to analyze data more efficiently.
With a powerful tool operating on AI, you can detect unusual patterns in user behavior and implement adaptive processes such as extra verification for transactions at odd hours, and implement risk-based authentications.
- Perform vulnerability assessments and penetration tests
Penetration testing uses active capabilities simulation instead of any evidence-based review. This means it looks into the actual performance of your security infrastructure rather than relying on guesstimates in admin reviews.
This is significantly important for small to medium businesses considering 82% of ransomware attacks hit SMBs, with more than half of these companies closing soon after. Security assessments can help identify your security’s weaknesses and ensures you’re well-prepared for the ever-evolving technology of cyber attacks.
- Monitor networks 24/7
There is a growing need for strong cybersecurity skills in the industry. With an estimated prediction of an almost 3 million shortage of cybersecurity professionals since 2018, it’s become even more crucial to have the right security controls and measures in place.
Find a good cybersecurity team that can effectively monitor and detect suspicious activity and attacks to keep your business safe.
Staying Vigilant of Cybersecurity Trends and Threats
Knowledge is power when it comes to protecting your business. The best way to be prepared for any type of cyber threat is to stay informed and proactive in your cybersecurity strategy.
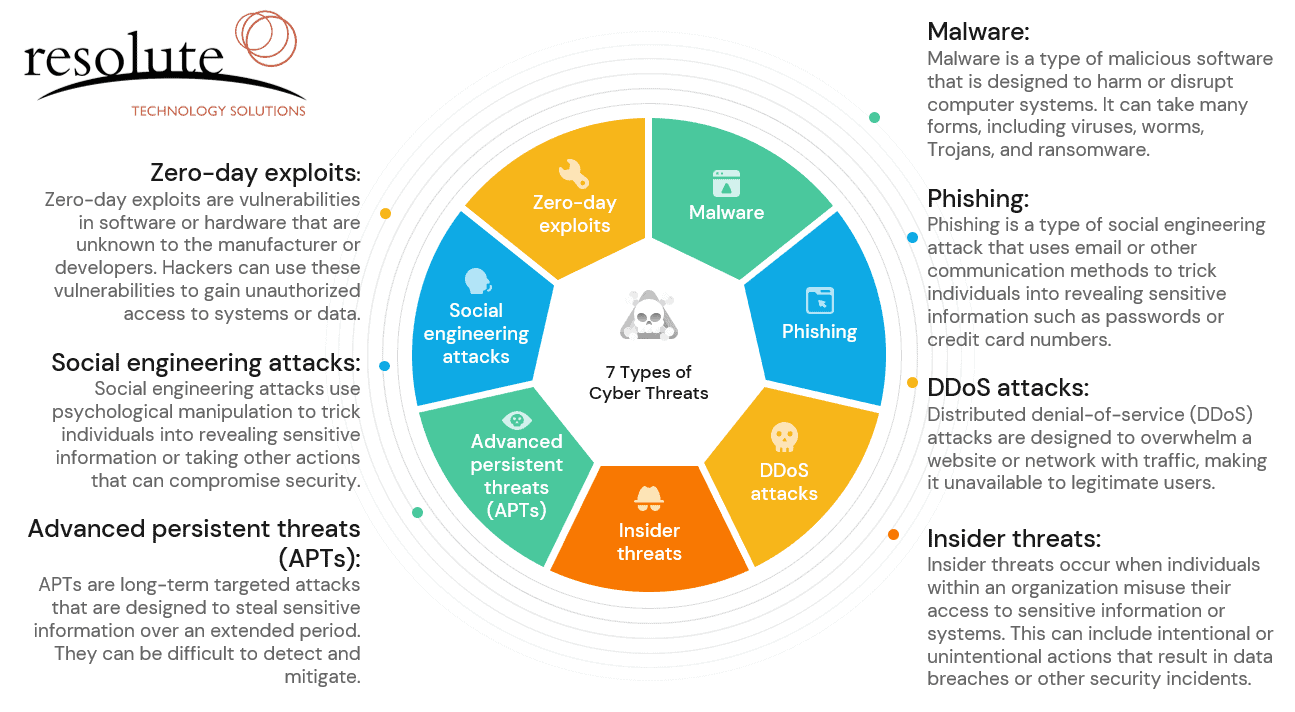
Here are some of the trends worth looking into as technology continues to develop.
AI and machine learning-related threats
AI and machine learning are useful tools for security, however this technology should never be underestimated. Malicious entities can exploit this for more sophisticated attacks with deepfakes, automated hacking, and adaptive malware.
Stay ahead of the game and utilize the best of AI for threat detection, response, and predictive analytics.
Quantum computing
Quantum computing poses a threat to cybersecurity. It can be used as a potential vehicle for data breaches, harvesting personal data, and ultimately, theft of digital assets.
Staying vigilant and prepared for post-quantum cryptography will help your organization in the long run.
Supply chain attacks
While it may seem like a small thing, services and providers are all interconnected. Malicious actors may exploit weak links. The vulnerabilities, for example, of one supplier can have a cascading effect. An attack that targets one supply chain can also target partner businesses.
Doing your due diligence in researching the teams for your essential services will go a long way.
Ransomware evolution
Ransomware attacks will likely grow more targeted and sophisticated. This means attackers can also leverage artificial intelligence to create more customized attacks for high-value businesses. It’s also important to consider that these cyber threats might encrypt data and use it as blackmail to acquire money in exchange.
Conclusion
Your organization’s cybersecurity maturity matters. Taking every precaution to protect and defend your assets will empower your business to withstand cyber attacks even when you least expect it.
Small to medium businesses are just as much at risk for cyber attacks as enterprises, even if their customer bases and data quantities largely vary. In a time when everything is accessible online, taking a more proactive approach to upgrading your cybersecurity strategy can give you a leg up on protecting your business. Ultimately, maintaining your business’s integrity and value requires a headstrong commitment to cybersecurity.